Community bug bounty program

At Hashstack, we have built a permissionless, zk-native money market protocol to enable under-collateralised loans upto 300% borrower’s capital. Built on Starknet L2, Hashstack leverages the capability of zero-knowledge proofs to provide a cost & capital-efficient lending solution.
Security is at the core of everything we do at Hashstack. We have spent the better part of this quarter to thoroughly review, test, stress-test the protocol design, code & our internal processes; including but not limited to cloud and private key security. As a part of these efforts, our team has painstakingly tested and ensured our contracts are secure from the
- Vulnerabilities listed in swc registry.
- DeFi vulnerabilities exploited between 2020–2023.
Additionally, Hashstack’s contracts are audited by Certik[Report]. However, as we prepare for the mainnet roll-out, we are opening up the task of helping us ensure we are to you, our community. Starknet is going through a critical transition from Cairo 0.1 to Cairo 1.0(Regenesis); implying, all the projects that are already live will have to upgrade their code to Cairo 1.0 in the next few months. Cairo 1.0 carries some major syntactical upgrades over cairo 0.10. This could mean that, we may discover a simpler way to execute the same logic with Cairo 1.0 effectively implying the possible need to rewire the protocol. In our attempt to strike a balance between our capital conscious approach and the need for a secure, safe protocol; we believed that the community is the best path at the moment.
Bounty Details
Total Prize Pool: $10,000 USDC.
Duration: 15 days
- Starts: 01 March, 2023. 12:00 am, UTC.
- Ends: 15 March, 2023. 11:59pm, UTC.
- Join the Hashstack Community here: https://discord.com/invite/hashstack
- Individual researchers can request code access from here: https://forms.gle/eK4K1DdboP82JPy68
- Teams can request code access from here: https://forms.gle/jaozcxukNrHWdHDh6
- Submit findings using this form: https://forms.gle/Z5Peb2dLYMTWVMyy7
To register a team, you must first register individually and then fill out this form: https://forms.gle/jaozcxukNrHWdHDh6
❗️Important note: Team awards are sent as a single payment to one wallet. We strongly recommend using a multisig wallet, to distribute awards among your team members. Note that Hashstack does not track which team member submitted each finding; your team is responsible for keeping track of that information and distributing awards. The team structure at Hashstack is designed so that you submit as a team and get paid as a team.
Program overview
The Community Bug Bounty program is divided into two phases based on the visibility of the Smart Contracts. We are currently opening the first phase of the program, where interested participants have to find the bugs in private repositories of Hashstack and report them to the Hashstack team to win bounties. We are working towards opening the codebase to everyone in the second phase.
This Community Bug Bounty program is focused on Hashstack smart contracts and is intended to evaluate the following
- Loss of funds.
- Redirection of funds.
- Denial of Service.
- Anomalistic behavior.
Community Bug Bounty Rewards Distribution
Rewards will be distributed based on the severity of the bug and its impact on the overall protocol as well as the difficulty in discovering such vulnerability. This will be a simplified 4-level scale to classify bugs and distribute the bounties.
Threat Level and reward distribution:
- Critical — upto $5000 & 2500xp points
- High — upto $3000 & 1500xp points
- Medium — upto $1500 & 750xp points
- Low — upto $500 & 350xp points
XP points are available in our crew3, which can be exchanged for Hashstack’s native tokens in the future. Do note that it won’t be 1–1 in value. We will release an official announcement about the same.
All the threat-level bug reports require a PoC (Proof Of Concept) and a suggestion to fix the bug to be eligible for the reward. Click on the form to submit a bug/fix: https://forms.gle/Z5Peb2dLYMTWVMyy7
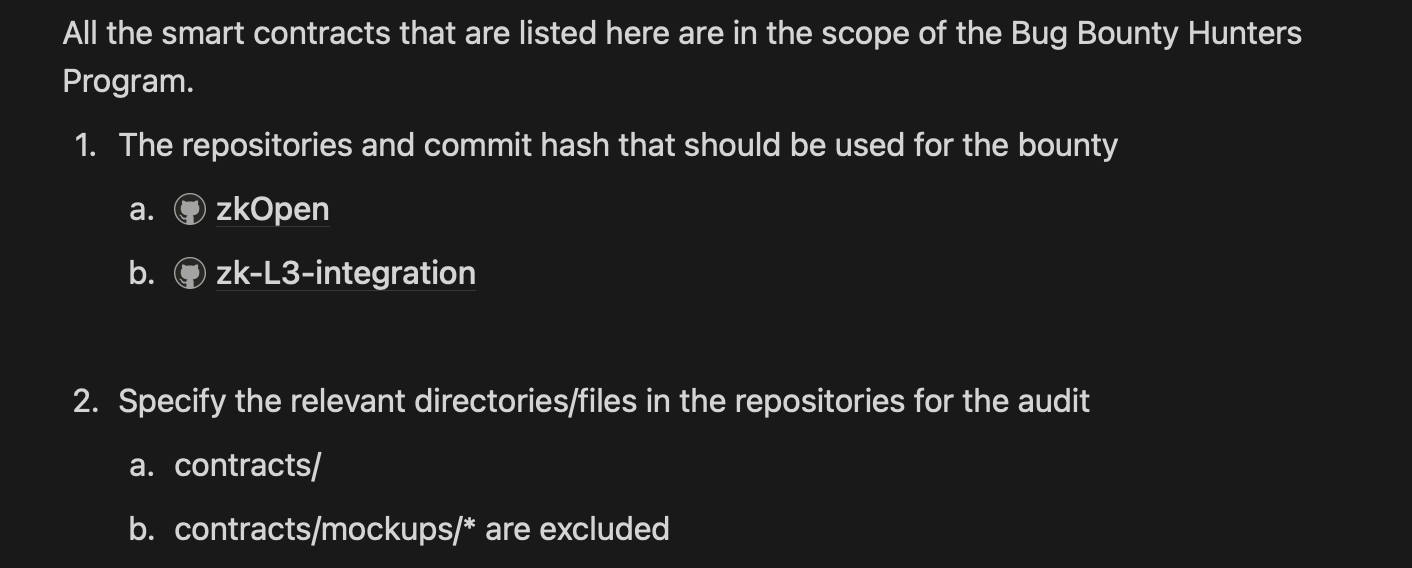
Assets in Scope
Answering some common questions
- If you have a public code repo, please share it here: available on request
- How many contracts are in scope?: All the contracts, as mentioned above, excluding mockups.
- What is the overall line coverage percentage provided by your tests?: TODO
- Is there a need to understand a separate part of the codebase / get context in order to audit this part of the protocol?:
- Please describe required context: Integrates with Myswap and Jediswap. Yagi in development and not supported in mainnet yet.
- Does the token conform to the ERC20 standard?: We aren't creating a new token.
- Are there any novel or unique curve logic or mathematical models?: DIAL : https://blog.hashstack.finance/deconstructing-hashstacks-dynamic-interest-algorithm-dial/
- Does it use a timelock function?: Yes, for Committed deposits withdrawal and loans collateral withdrawal
- Is it an NFT?: No
- Does it have an AMM?: We integrate with an AMM
- Is it a fork of a popular project?: No
- Does it use rollups?: yes, ZK Rollups
- Is it multi-chain?: No
- Does it use a side-chain?: No
Disclosure, Reporting Guidelines and Prohibitions
We ask that all Community Bug Bounty program participants should:
- Report vulnerabilities as soon as they have been discovered and keep them confidential between yourself and the Hashstack team until the issue(s) has been resolved.
- The security researcher must give a grace period of 7 days to revert on their identified bugs before they can disclose them to the public.
- Do not involve privacy violations, user experience degradation, and disruption to production systems during security testing.
- The project developers will determine the severity of the bug.
This Community Bug Bounty program prohibits the following activities:
- Any automated testing of services generates significant amounts of traffic.
- Any phishing attempt or other social engineering attacks against our employees or customers.
- Any testing with mainnet or public testnet contracts. (All testing must be on private testnet only)
- Public disclosure of an unpatched vulnerability in an embargoed bounty.
Eligibility & Out of Scope
Only specific exploits and vulnerabilities related to Hashstack smart contracts listed in scope are eligible for a reward.
In-scope
- Malicious Input Handling.
- Arithmetic.
- Escalation of privileges.
- Loss of user funds.
- Theft of funds.
- Freezing of funds.
- Unable to call smart contract.
- Smart contract fails to deliver promised returns.
- Withdrawal of funds more than allowed.
- Loss of funds during loan utilization interaction with zk-l3-interaction repo and 3rd party dapps.
Out-of-scope
The following vulnerabilities are excluded from this bug bounty program.
- Attacks that the reporters have already exploited themselves, leading to damage.
- Attacks requiring access to leaked keys/credentials.
- Attacks requiring access to privileged addresses.
- Issues found by the Hashstack team. It will be listed in GitHub issues or a separate bug list.
Any duplicate bug(s) that we have added to our bug list will not be considered for bounty. Access the list of bugs here: https://hashstack.notion.site/Community-Bug-Bounty-List-of-Known-Bugs-002ee899da814824b38306354ea2af3d
To be eligible for bounty of different threat levels, you should demonstrate the impact of the exploit. Wherever the attack is profitable, freezing of protocol or funds should significantly impact the protocol and its users.
This Community Bug Bounty program prohibits the following activities
- Any automated testing of services generates significant amounts of traffic.
- Any phishing attempt or other social engineering attacks against our employees or customers.
- Any testing with mainnet or public testnet contracts. (All testing must be on private testnet only)
- Public disclosure of an unpatched vulnerability in an embargoed bounty.
To be eligible for bounty of different threat levels, you should demonstrate the impact of the exploit. Wherever the attack is profitable, freezing of protocol or funds should significantly impact the protocol and its users.
Quickstart
- Git clone: https://github.com/0xHashstack/zkOpen
- Git clone: https://github.com/0xHashstack/zk-L3-integration
See Readme files in github repo for detail instructions
Install dependencies
- run - `npm install`, `pip install cairo-nile`
- Setup cairo env from : `https://www.cairo-lang.org/docs/quickstart.html#`.
Check below for version details.
Ensure cairo venv is at `~/cairo_venv`
- Install protostar from `https://docs.swmansion.com/protostar/docs/tutorials/installation`.
Check version details below.
node: 16.14.0
cairo: 0.10.3
starknet-hardhat-plugin: , auto managed in package.json
devnet: 0.3.0
@OpenZeppelin/cairo-contracts: auto managed in protostar.toml
protostar: 0.9.1
Build
- npm run compile
Protostar Tests Tests need to be run one by one. Fuzzy tests are included. Run protostar install the first time running tests. Add path of test script to protostar test tests/* like below-: Remember to include --disable-hint-validation to avoid errors regarding hints in codebase
protostar install
protostar test tests/test_* --disable-hint-validation
Static Analysis
Not present
Coverage
Not present
Kindly Note
- Turn in your reports before the contest end time.
- Submit your Medium and High-risk findings individually.
- Bundle all of your low-risk and non-critical findings into a single QA report. Attach the link in the forms.
- There is no limit on submitting the bugs through the google form.
